The satellite eavesdropping stations of Russia’s intelligence services (part 2)by Bart Hendrickx
|
| All of the GRU and KGB eavesdropping stations have a wide variety of parabolic dish antennas. |
All or some of these were built by the OKB MEI design bureau in Moscow in cooperation with an institute in Rostov-na-Donu (now known as the Rostov-na-Donu Research Institute for Radio Communications or RNIIRS). The biggest, the TNA-400, was a modified version of an antenna that had been built near Simferopol in Ukraine in the early 1960s to communicate with Soviet lunar and interplanetary probes. (In addition to that, it was also used to eavesdrop on communications between the Apollo astronauts and Mission Control in Houston under a secret program known as Poisk, or “search”.) As mentioned in part 1, the TNA-400 and TNA-110 antennas near Ventspils were refurbished for astronomical observations after the collapse of the Soviet Union, and renamed RT-16 and RT-32. As far as can be assessed, the big Soviet-era antennas at the site near Yakovlevka continue to be used for satellite intelligence today.
 The 32-meter TNA-400 antenna at the GRU site near Yakovlevka. It was repainted sometime after this photo was taken. Source: Russian social media. |
The biggest antenna currently seen at the other GRU sites is a roughly 25-meter antenna at the station in Toivorovo in the St.-Petersburg region. Several have antennas measuring around 16 and 12 meters, some of them placed on circular control buildings very similar to the ones used as part of the Soviet-era ground stations for the Molniya communications satellites. Some could be further modifications of the TNA-210, TNA-110, and TNA-97 antennas originally conceived in the Soviet days. These types are all mentioned in a 2015 article by RNIIRS that discusses improvements in their performance. [2] Smaller antennas of varying sizes are also seen at the GRU stations. Since communications satellites have become much more powerful over the decades, their signals can now be received by antennas up to ten times smaller than the ones needed originally.
 The 25-meter dish antenna at the GRU’s Zvezda station 41480 in Toivorovo. Source: Russian social media. |
All that is known about the antennas at the Soviet-era KGB sites is from the declassified 1983 CIA report, which gives antenna diameters of 25, 12, and 7 meters. Antennas of those sizes are still seen at the FSB sites today in addition to 16-meter antennas and smaller ones. The 25-meter antennas are at only two sites, namely the ones in the Khabarovsk region and in Crimea. One PhD dissertation that can be linked to the FSB sites mentions antennas named TNA-7, TNA-7M, TNA-9, TNA-12, and TNA-16, with the numbers denoting their diameters. [3]. Antenna names seen in procurement documents related to the FSB sites are Kentavr, Tantal, Persei, Eskort, and Rebus. Among the companies involved in building these antennas are NII Radio, OKB MEI, and NPP ATS.
It is perfectly possible that there is commonality between the hardware used at the GRU and FSB stations. For instance, the 25-meter antenna at the FSB station near Alushta in Crimea is identified in tender documentation as TNA-210-K, indicating it is a further development of the TNA-210 antenna used in the GRU’s Zvezda network. [4] Remarkably, very few of the parabolic antennas seen at the GRU and FSB sites are covered by radomes, which would protect them against harsh climatic conditions and also conceal their orientation. It should be noted that at least some of the antennas seen at these facilities may also provide orthodox satellite communication for their host sites.
Apart from traditional parabolic antennas, a handful of the sites also have so-called multiple beam torus antennas (MBTA). Whereas parabolic antennas can only receive signals from one satellite at a time, MBTAs are capable of simultaneously intercepting signals from multiple satellites. They are seen at the GRU site in Klimovsk, the FSB site in Dubovyy Rynok, and the former KGB site in Dobroaleksandrovka (now owned by Ukraine. A 30-meter MBTA was constructed in Klimovsk around 2005–2006, followed by a somewhat smaller one measuring about 15 meters around 2017 (see the picture heading this article.) A similarly sized antenna appeared at the site in Dubovyy Rynok sometime between 2006 and 2011 and can be seen in the satellite picture of this station in part 1. This may be a multibeam antenna that in some procurement documents is referred to as Veyer (“fan”).
The station in Dobroaleksandrovka sports a massive 80-meter MBTA, the biggest of its kind in the world. Nicknamed “The Comb”, it is believed to have been constructed back in 1987 and must have been one of the crown jewels of the KGB’s satellite eavesdropping network. A smaller 17-meter MBTA was erected by the Ukrainians themselves in 2009–2010. Whether any of these are still intact after a reported Russian strike in March 2024 is unknown.
Multiple beam torus antennas are also present at several of the listening posts operated by America’s National Security Agency outside the US. The first one appeared around 2007, which, remarkably enough, was twenty years after the Russians began using such antennas for this purpose at the site in Dobroaleksandrovka. They can have an arc of view of up to 75 degrees, enabling them to receive satellite transmissions from as many as three dozen geostationary satellites at the same time without degradation in performance. Moreover, a large number of transponders on all of these satellites can be monitored simultaneously. [5] Several patents published by the FSB Academy in recent years describe similar antennas capable of receiving transmissions in the C-, Ku-, and Ka-bands from several satellites, although an exact number is not given. [6]
 Massive 80-meter MBTA at the site in Dobroaleksandrovka, Ukraine (photo taken in 2008). Source |
Articles that are almost certainly related to the FSB’s satellite interception stations provide some insight into the challenges they face when observing satellites in geostationary orbit. Geostationary satellites appear relatively low in the sky from Russian territory, especially from locations in the north of the country. Since the antennas must be pointed close to the horizon, they are more susceptible to background interference. Some of the papers discuss ways of improving their signal-to-noise ratio to overcome that problem. One experiment conducted as part of this research involved picking up signals from a radio beacon installed aboard Intelsat 10-02. [7] Other FSB research conducted early last decade focused on techniques to pick up signals with frequencies up to three gigahertz from geostationary satellites that are on the edge of visibility from Russian territory. [8]
| А key question is what satellites the eavesdropping stations are looking at and what kind of information the Russians are trying to extract from them. |
A strange feature is seen at the GRU sites in Maksimovshchina and Kaliningrad. It consists of what looks like a radome surrounded by five identical structures. At the location in Maksimovshchina, the construction first shows up in Google Earth imagery from September 2016, with no sign of it in the preceding imagery from June 2015. In Kaliningrad, the building process was much slower. The five “petals” appeared first in April 2014, followed only four years later by the central structure. These features so far defy explanation. They may have nothing to do with satellite intelligence.
 Unexplained feature at GRU site 25137 in Kaliningrad. Source: Google Earth. |
Target satellites
А key question is what satellites the eavesdropping stations are looking at and what kind of information the Russians are trying to extract from them. All that can be learned from Russian sources are some details on the targets of the GRU’s Zvezda network in the Soviet days.
A GRU officer who served at Zvezda unit 51430 near Yakovlevka in Russia’s Far East in the late 1970s and early 1980s described the functions of the three originally built antennas there as follows:
- TNA-400: intercepting signals of Intelsat IV communications satellites at frequencies up to 4200 megahertz
- TNA-110: intercepting signals of US military communications satellites at frequencies up to 7800 megahertz
- TNA-97: intercepting signals of foreign reconnaissance satellites at frequencies up to 2500 megahertz [9]
This is more or less consistent with what one other veteran has written about the functions of the three antennas. According to him, one was needed to “gather information about the on-board equipment of detected satellites,” by which he probably referred to efforts to learn more about the design and functioning of reconnaissance satellites through analysis of intercepted signals. The other two, in his words, were used “in the interests of the GRU and the KGB,” by which he presumably meant interception of voice traffic from both military and civilian communications satellites. [10] In other words, the original objectives of Zvezda were both to collect information about foreign satellites, which falls under the domain of electronic intelligence or ELINT, and from foreign satellites, which belongs to the field of communications intelligence or COMINT. (SIGINT is an umbrella term for the two.)
ELINT of foreign satellites would have been needed to fulfill what seems to have been a key initial objective of Zvezda, namely, to identify potential targets for anti-satellite attacks (see part 1.) The question is what those targets could have been. The demonstrated ceiling of the Soviet “IS” interceptor satellites was about 1,000 kilometers, so any targets would have been restricted to orbits lower than that. The most obvious ones were photographic reconnaissance satellites, but these are not known to have communicated with any ground stations in the vicinity of the Soviet Union.
One piece of information indicates that a possible target for Zvezda were US signals intelligence satellites in geostationary orbit. According to one source, one of the original functions of the Zvezda site near Ventspils in Latvia was to pick up signals downlinked by US satellites to ground stations in England. [11] This must have been a reference to Menwith Hill in Yorkshire, a major US signals intelligence base used not only to intercept traffic from foreign communications satellites, but also to control US signals intelligence satellites in geostationary orbit. The TNA-97 antenna said to have been used for ELINT of reconnaissance satellites was not only in Yakovlevka, but in Ventspils as well. Its frequency range (“up to 2500 megahertz”) suggests it could only have picked up telemetry from these satellites, which is typically transmitted at such low frequencies. The intelligence information itself was reportedly sent to Earth with a narrow-beam antenna at a frequency of 24 gigahertz (which corresponds to 24,000 megahertz.) [12]
| All indications are that the primary objective of the eavesdropping stations was to collect COMINT. |
As far as is known, Menwith Hill began to be used as a control station for SIGINT satellites with the introduction of the CHALET COMINT satellites in 1978. It is possible, however, that Ventspils also monitored the preceding series of geostationary SIGINT satellites. Called CANYON, these were launched between 1968 and 1977 and controlled from a station in Bad Aibling in West Germany, which was significantly closer to Ventspils than Menwith Hill. It is not clear which reconnaissance satellites the station in Yakovlevka could have been eavesdropping on. Situated not far from the USSR’s Pacific coast, it was nowhere near any ground stations for US reconnaissance satellites. Of course, geostationary SIGINT satellites were way out of reach of the Soviet Union’s interceptor satellites. Based on the available information, one can only assume that Zvezda’s original goal of identifying ASAT targets soon receded into the background.
All indications are that the primary objective of the eavesdropping stations was to collect COMINT. For the KGB, that must have been the sole goal from the very outset since it would have had no interest in ELINT of military satellites. Intelsat satellites can be positively identified as Soviet-era targets not only for the Zvezda station near Yakovlevka, but also for the one near Ventspils. [13] The interest in these satellites is not surprising. Having debuted in 1965, they were the only international telecommunications satellites until the early 1980s and were responsible for the vast majority of communications traffic between countries and continents. In addition to civilian traffic, they also carried diplomatic and government communications, which would have been of particular interest to intelligence agencies. The foundation of Intelsat in 1964 was one of the main driving forces behind the creation of the US National Security Agency’s network of COMINT stations and this may well have been the case for its Soviet equivalent as well.
By the time the Soviet listening posts became operational in the 1970s, Intelsat satellites provided global coverage. The Intelsat IV and IVA series launched during that decade had so-called “global beams” that covered the Atlantic, Pacific, and Indian Ocean areas as well as “zone beams” that covered smaller areas, more particularly the eastern US, the western US, western Europe, and eastern Asia. As can be seen on the map below, the NSA needed only four COMINT stations to monitor all those beams. [14]
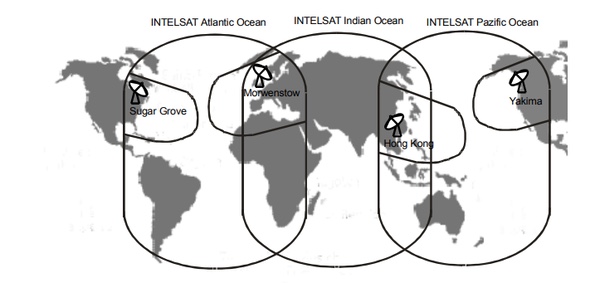 NSA coverage of Intelsat global and zone beams in the 1970s. Source |
Since the global beams overlapped each other over the Soviet Union, they could all be seen by the Soviet network, which stretched all the way from the country’s western to its eastern borders. The zone beams covering western Europe and eastern Asia were visible from stations in the western and eastern parts of the Soviet Union. Additional coverage of the East Asia beam may have been provided by the GRU Zvezda stations in Vietnam and Burma. The zone beam covering the western US was possibly just within range of the station in Lourdes, Cuba, but the one covering the eastern US was out of sight. The situation became much more complex in the 1980s and later with the emergence of new international satellite operators such as Eutelsat and Inmarsat and the increased use of narrow spot beams, many of which did not spill over into Soviet territory.
The Intelsat IV and IVA satellites operated in C-band with downlink frequencies between 3700 and 4200 megahertz. The low power of C-band transmissions initially required the use of big parabolic antennas like the 32-meter TNA-400 near Ventspils and Yakovlevka. Later, as technology evolved, such signals could also be received by antennas smaller than 10 meters. Such antennas were also sufficient to pick up higher frequency signals in the Ku-band, which gained popularity in the 1980s.
The claim that the Zvezda network was also intended to monitor military communications satellites is corroborated by one account of its use to intercept signals from the second-generation satellites of the US Defense Support Communications System (DSCS II). These began flying in 1971 and downlinked signals in the X-band. The reported frequency range of the 16-meter TNA-110 antenna (up to 7800 megahertz) was indeed in the lower part of that band. When Soviet intelligence officials became aware of plans to launch the DSCS II satellites, they tasked specialists of the TsNII-18 military research institute with designing a so-called low-noise amplifier that could be used to receive signals from DSCS II satellites parked over the Atlantic and Indian Oceans. The device was installed at the Zvezda station in Chabanka (Ukraine), which only had a 12-meter diameter dish antenna, not the 16-meter TNA-110. According to the account, it took nearly a week to detect the first signals from a DSCS II satellite because neither the exact location of the satellite nor its precise downlink frequencies were known. The intercepted data reportedly included critical information on the activities of the US State Department and the US Strategic Air Command. [15] The veteran of the Zvezda unit near Yakovlevka recounts how his team monitored joint military exercises staged by the US, Japan, and South Korea in the Pacific. This may also have been done by listening in on US military communications satellites.
The few declassified CIA documents that deal with the Soviet stations reveal very little about what US intelligence knew about their target satellites. They mention only communications intelligence, with one report in 1982 specifically singling out monitoring of the Intelsat network by both the KGB and GRU. Another report, released in 1977, stated that the facility near Ventspils was responsible for “intercept of US space vehicles [including Skylab].” [16] One other sign that the stations may also have monitored American piloted space missions comes from the memoirs of the Yakovlevka veteran, who writes that his team kept track of the first flight of the Space Shuttle in April 1981. It is not clear what kind of information the Russians may have been trying to gather by doing so, although there may have been particular interest in the dedicated military Shuttle missions that were later flown.
COMINT seems to have been the sole goal from the outset of the equivalent program run by America’s National Security Agency. As became known from documents leaked last decade by Edward Snowden, the NSA program, which had the umbrella name FROSTING, was set up in 1966, the same year that the GRU’s Zvezda program officially got underway. It consisted of two sub-programs. One, named TRANSIENT, targeted Soviet satellites, mainly Molniya communications satellites, which were used for both government and military communications. The other, called ECHELON, was intended to covertly intercept transmissions from Intelsat satellites. The two parallel operations were later merged into a global system called FORNSAT (foreign satellite intelligence).
ECHELON’s main goal was to eavesdrop on non-military targets such as governments, organizations, businesses, and private persons in virtually every country of the world, including US allies. Rather than snooping on specific individuals, ECHELON worked by indiscriminately intercepting very large quantities of communication and then siphoning out whatever was valuable with the help of computer algorithms. This mode of operation, called “Collect-it-all,” was later facilitated by the introduction of multiple beam torus antennas, which can simultaneously monitor signals from several dozen satellites. An important reason for the NSA to introduce such antennas was to increase access to global Internet traffic carried by satellite. [17]
| There was little cooperation between them in their respective SIGINT endeavors and that division-of-labor agreements were not always respected. For instance, it was not uncommon for both the KGB and GRU to operate clandestine intelligence radio intercept stations inside the same Russian embassies around the world. |
There is no publicly available information on the satellites that the GRU and FSB stations are monitoring these days. The GRU may continue to have an interest in reconnaissance satellites since the TNA-97 antennas used for that purpose in the 1970s (or modifications thereof) still seem to be in use. The NSA base in Menwith Hill, England, still serves as a control center for US geostationary SIGINT satellites, but there is no way of telling if those are still a target for the Russian listening stations. As for military communications satellites, the advancement of data encryption techniques must have gradually made the interception of data from such satellites much more difficult. The primary focus is most likely on the vast array of commercial communications satellites that now populate the geostationary belt. Whether the Russians also use the “Collect-it-all” technique is open to speculation. While a handful of the stations have multibeam torus antennas, the computer technology needed to process the data may not be as advanced as that used by the NSA.
By looking at antenna orientations in the Google Earth imagery, it is possible to determine that the Russian network covers a part of the geostationary belt stretching from roughly 180°E to 20°W, which is just about all that can be seen from Russian territory. By contrast, the network that the NSA operates jointly with international partners is spread across the world, both in the northern and southern hemispheres, and offers global coverage. Research carried out in 2015 showed that at the time it consisted of 14 stations and a total of about 232 antennas. [18] Russia’s gap in coverage may at least partially be compensated by the interception of satellite data with parabolic antennas mounted on rooftops of embassies. These are seen on Russian embassies around the world and at least some of them may be used to collect COMINT from satellites.
Using an app called dishpointer (intended to align home satellite dishes), one can get a rough idea of the kind of satellites that the antennas at the GRU and FSB sites are pointing at. There appears to be a continued interest in Intelsat satellites, with other popular targets being satellites operated by Eutelsat and Inmarsat. One report in 2008 singled out the Inmarsat 4-F2 satellite as a likely target of observation for the FSB station (nr. 49911) in the Pskov region near Estonia. [19] That satellite has since been relocated to a new spot that puts it out of reach of this station, but judging from antenna orientations, a new target for the station may be Inmarsat-GX5 at 11.0°E, whose footprint reaches just across Estonia’s border with Russia. Stations in central and eastern Russia seem to have some of their antennas pointed at satellites owned by Chinese operators.
One other question to be addressed is why it was decided to have two independent networks run by the GRU and KGB/FSB. Many of the stations were and still are in the same general area and, consequently, in the same satellite footprints. A case in point are the now decommissioned stations that both intelligence agencies had in Georgia (nr. 51868 and 61615), which were barely six kilometers apart.
Considering their background, it would be logical to assume that the GRU has focused exclusively on military satellites and the KGB/FSB on government/commercial satellites. However, things are probably not as straightforward as that. As pointed out in one history of Soviet SIGINT activities, the historically rooted inter-service rivalry between the two organizations meant that there was little cooperation between them in their respective SIGINT endeavors and that division-of-labor agreements were not always respected. For instance, it was not uncommon for both the KGB and GRU to operate clandestine intelligence radio intercept stations inside the same Russian embassies around the world which often monitored the same targets without any coordination of effort whatsoever. [20] Similarly, there may be at least some overlap in the targets observed by the satellite COMINT stations, however wasteful that may seem to be.
The FSB also appears to operate a space-based COMINT collection system that is most likely seen as an extension of its ground-based network. It consists of two satellites, launched under the official names Luch and Luch-5X in September 2014 and March 2023, respectively. They have since been traveling across the geostationary belt, regularly parking themselves close to foreign government and commercial communications satellites, with satellites operated by Intelsat and Eutelsat also being prime targets. The two satellites, which are internally named Olimp and Yenisei-2, were discussed in detail in an earlier article here, which provided evidence that they are operated by the FSB’s 16th Center. [21] One or more payloads of the satellites are provided by a company named NII Radio, which has close ties with the 16th Center and also manufactures some of the antennas used in the FSB’s ground-based COMINT network. It is very well possible that the data intercepted by these satellites are sent to one or more of the FSB’s COMINT collection sites on Russian territory. Likewise, the data obtained by the equivalent American PAN and NEMESIS satellites are downlinked to the US SIGINT base in Menwith Hill in England.
 A drawing possibly showing the Luch/Olimp eavesdropping satellite. Source: ISS Reshetnev. |
Luch/Olimp has been parked close to Intelsat-37E since the summer of 2022, a possible sign that it is running low on propellant. The newer satellite, Luch-5X/Yenisei-2, is still very active, relocating itself to a new target satellite every few months. In April to June last year it loitered right next to Astra A4, a satellite belonging to Luxembourg-based satellite operator SES that relays a number of Ukrainian TV channels. Some of those were jammed shortly before and after Luch-5X’s arrival, but all indications are that the jamming was caused by ground-based emitters on Russian territory and not the Luch-5X satellite itself. Other Western communications satellites have also fallen victim to such electronic attacks without any of the Luch satellites being in the neighborhood. (For completeness’ sake, it should be added that there have also been reports of Russian satellite-relayed broadcasts being jammed by Ukraine.)
Unlike the ground-based COMINT collection stations, which can receive only downlink, the Luch satellites should be capable of intercepting signals uplinked to target satellites. This has several possible advantages. It would enable them to geolocate transmitters as well as chart uplink frequencies, which in turn could help jam some of the transponders. Besides that, they should be capable of monitoring traffic that cannot be picked up by the ground stations. Only some of the downlink beams of the target satellites are visible from Russian territory. Instead of employing wide beams, modern high-throughput communications satellites utilize multiple spot beams to cover relatively small service areas. There is evidence that at least one payload aboard Luch-5X is designed to pick up such narrow beams at Ka-band frequencies and then convert them to L-band for downlink to ground stations.
 Luch-5X (named Luch/Olymp 2 here) parked next to Astra A4 in April 2024. Source |
New efforts to collect ELINT on foreign satellites
While the GRU and FSB stations are mainly or exclusively aimed at collecting COMINT, several new systems have been introduced in recent years to gather electronic intelligence on foreign satellites. These are not operated by the intelligence services. Instead, they have been developed as part of Russia’s space surveillance network, which keeps a constant eye on events in Earth orbit. It has independent military and civilian components (the Ministry of Defense’s SKKP network and Roscosmos’ ASPOS OKP network) and consists primarily of radars operated solely by the military and optical telescopes operated by both the military and Roscosmos. However, unlike space surveillance systems of other nations, it also includes several ELINT systems.
Part of SKKP are systems named Moment and Sledopyt (“pathfinder”), which are described in official documents as being used for “monitoring radio emitting satellites.” Moment comprises a single facility near SKKP’s headquarters in Noginsk-9 (some 60 kilometers northeast of Moscow) and Sledopyt numbers four sites (in Noginsk-9, the Kaliningrad region, Siberia, and the Far East, the final one still being under construction.) Based on available information, Moment and Sledopyt are probably designed to learn more about the purpose and design of foreign satellites through analysis of intercepted signals. They can also assist in tracking satellites in daylight, if they are obscured from view by clouds at night or if they orbit too high to be detected by radars. Moment has been operational since about the turn of the century. Sledopyt, assigned to NII Radio back in 2009, has clearly suffered many delays and looks like it has been scaled down. [22]
| The locations in Mexico and Cuba would possibly enable KRTM to intercept telemetry from rockets launched from Vandenberg Space Force Base in California and Cape Canaveral in Florida respectively. |
In 2019, the Ministry of Defense ordered another company, PAO Radiofizika, to build a system called KRTM (“Complex for Radio-Technical Monitoring”). According to procurement documentation, its goal is to monitor telemetry from rockets and satellites at altitudes from 80 to 70,000 kilometers and between frequencies of 2.2 and 2.4 gigahertz. It is based on a system named Telemetr that PAO Radiofizika developed earlier to pick up telemetry from launches of US intercontinental and submarine-launched ballistic missiles. The plan was for KRTM to be co-deployed with a set of telescopes of Roscosmos’ ASPOS OKP network and for the two to work together as a so-called Integrated Observation Complex (OKN). OKN would first be installed at a temporary location in Russia (apparently for testing) before being moved to the Guillermo Haro Observatory in northwestern Mexico or to an unspecified place in Cuba, giving it access to objects that are impossible or more difficult to spot from Russian territory.
As can be seen in Google Earth imagery, OKN was deployed in a mountainous region near the village of Doliny, some 70 kilometers north of Vladivostok in Russia’s Far East. It featured several telescopes as well as a white building with a rounded roof that may have acted as a protective enclosure for the KRTM system. The latest imagery from June 2024 shows that the enclosure and some of the telescopes have been dismantled, a possible sign they have been or are being moved to one of the two locations abroad, with Cuba being a more likely candidate given the current geopolitical situation. The locations in Mexico and Cuba would possibly enable KRTM to intercept telemetry from rockets launched from Vandenberg Space Force Base in California and Cape Canaveral in Florida respectively. It is worth noting that the site near Doliny is right under the flight path of some rockets launched from Baikonur and Plesetsk. These may have served as targets for telemetry intercepts by the KRTM system. [23]
 The OKN site near Doliny in Russia’s Far East in May 2023. Source: Google Earth. |
Finally, another space-related ELINT project was initiated by the Ministry of Defense in 2020 under the name Nast-R and assigned to MAK Vympel. It has been described in court documentation as “a network of assets to monitor space-based radar systems”. MAK Vympel has published several technical articles that are probably related to Nast-R. They mention a radar monitoring system that would make it possible to determine the carrier frequency, bandwidth, modulation type, pulse repetition frequency and the polarization of satellite radar signals and also to estimate the satellite’s ground swath.
One of MAK Vympel’s subcontractors for Nast-R (NII STT) has done research on electronic countermeasures against radar satellites, more particularly on a method called radar deception, which involves confusing enemy radars by generating false targets. This raises the possibility that Nast-R is intended to provide data for electronic warfare against radar reconnaissance satellites flying over Russian territory, preventing them from imaging targets of interest. It is not known if any elements of Nast-R have been deployed yet, but there are indications that it uses relatively simple off-the-shelf technology and that MAK Vympel has supplied similar radar monitoring systems to a foreign customer. [24]
References
- Some details on the Soviet-era GRU antennas are given by the sources summed up in reference 1 in part 1 of this article as well as in a history of the OKB MEI design bureau that is no longer online.
- Article by specialists of RNIIRS published in 2015.
- Summary of PhD dissertation published in 2020. The full version is no longer online. It refers to the Rebus-2T antenna (built for the FSB by NII Radio) and was supervised by professor Anatoliy Somov, who can be linked to the FSB Academy.
- Tender documentation published in May 2019.
- D. Ball et al, Expanded communications satellite surveillance and intelligence activities utilising multi-beam antenna systems, Nautilus Institute for Security and Sustainability, 2015.
- Four such patents were published by the FSB Academy in 2022 (1, 2, 3, 4).
- See reference 3.
- Two patents published in 2012 (1, 2). These are owned by the NII Radio company, but one of the patent holders is the FSB Academy’s Anatoliy Somov.
- Memoirs of GRU veteran Oleg Krivopalov, 2011, p. 381–382.
- Memoirs of SNII 45 veteran Aleksandr Gorelik, p. 375. Although not mentioned by Gorelik, ELINT of US reconnaissance satellites was most likely also in the interests of the GRU.
- See reference 10.
- The 24 GHz frequency is given in: Report on the existence of a global system for the interception of private and commercial communications (ECHELON interception system), European Parliament, 2001, p. 35.
- Recollections of a veteran of the Zvezda unit near Ventspils, 2021.
- See reference 12.
- History of the GRU’s SIGINT activities by Mikhail Boltunov, 2011, p. 158-159.
- The technology acquisition efforts of the Soviet intelligence services, CIA report, June 1982, p. 21; Similarity between electronics facilities at Lourdes, Cuba, and Vicak, USSR, CIA report, October 1977, p. 1.
- Article on the website of investigative journalist Duncan Campbell ; Reference 5.
- See reference 5.
- Snooping on Russia’s secret satellite snoopers, Politico, April 9, 2008.
- M. Aid, Eavesdroppers of the Kremlin: KGB SIGINT during the Cold War, chapter published in: K. De Leeuw, J. Bergstra, The history of information security, 2007.
- B. Hendrickx, Olimp and Yenisei-2: Russia’s secretive eavesdropping satellites, part 1 (November 20, 2023), part 2 (November 27, 2023).
- B. Hendrickx, Russia gears up for electronic warfare in space (part 2), The Space Review, November 2, 2020 ; Sledopyt thread on the NASA Spaceflight Forum.
- Thread on the Russian space surveillance network on the NASA Spaceflight Forum, Reply 8. The latest Google Earth imagery of the OKN site is here.
- Thread on the Russian space surveillance network on the NASA Spaceflight Forum, Replies 4 and 5.
Note: we are now moderating comments. There will be a delay in posting comments and no guarantee that all submitted comments will be posted.
